Are you walking the walk? SaaS Security is more than saying you care
Saying you care about saas security isn’t enough. External and internal security risks require constant effort to ensure compliance. YCBM has seen the benefits.

Kate Reynier

Not long ago I had an eye-opening conversation...
I was speaking with the customer service rep of a SaaS company about a support ticket I had raised, and she sent through a screen recording of the settings I needed to solve the problem. That should have been it.
But, in this video, it was clear that the support team for this company had full access to every area of my account - including data that contained personal information about all of our employees.
Me: “Do you have unrestricted access to our data?”
Rep: ”Yes. But We Take Privacy Very Seriously.”
Me: “That’s great to hear ... I’d like to cancel my account.”
This true story from YouCanBook.me CEO and co-founder Bridget Harris could probably happen with hundreds of other companies that you use every day. It was a lightbulb moment for her.
“Just saying "Privacy is very important to us" doesn’t mean your systems are safe. It’s totally meaningless if you don’t back it up with internal practices to ensure that data is secure,” she says.
“You can say all you want that you care about security and data. What really matters is: Who's got access to your data? How do you protect data?”
It was a timely interaction for Bridget who, as the CEO of a SaaS tool with customers around the world, was working through some big decisions about how best to implement data security practices and ensure compliance with global standards.

“A couple of different factors came together to push SaaS Security quickly up to the top of our agenda,” says Bridget.
“The first thing that really brought us to awareness of how we treated data was GDPR in 2018. We had to make a couple of changes there, like allowing customers to delete data, things we hadn't really thought through before — we were moving so fast and it was easy to say, ‘we’ll deal with that later’. GDPR forced us to say, ‘No, we're going to deal with that now.”
In case you weren’t paying attention back in May 2018, the EU’s General Data Protection Regulation (GDPR) had a huge impact on businesses of every size, in almost every country around the world. Any organization that dealt with European data had to have procedures to protect data and give customers and employees control over their own personally identifiable information (PII).
“GDPR had a huge impact. All of a sudden, we had a deadline to comply with some of the strictest privacy laws ever. You could no longer just say data privacy is really important to us. It's either a yes or no: you either secure it or you don't secure it. People either have access to it or they don't have access to it.”
Listening to customers
The second factor was less about being forced to comply with external laws, and more about doing everything they could to meet customer expectations.
“Over the years our customer base has changed to include more enterprise-level teams working in large corporations. We could see our customers were working through their own audits to ensure the tools they were using met their security requirements.
“We received a number of security questionnaires all asking similar questions, which forced us to think: If you have to answer no to a question — saying that you don't do something — then you have to ask yourself, ‘Well why not? Why don't we do that?’”
After her experience with the customer support rep, Bridget knows how it feels for any customer — not just Enterprise customers — who need to see that YouCanBook.me has the processes in place to earn recognized security credentials.
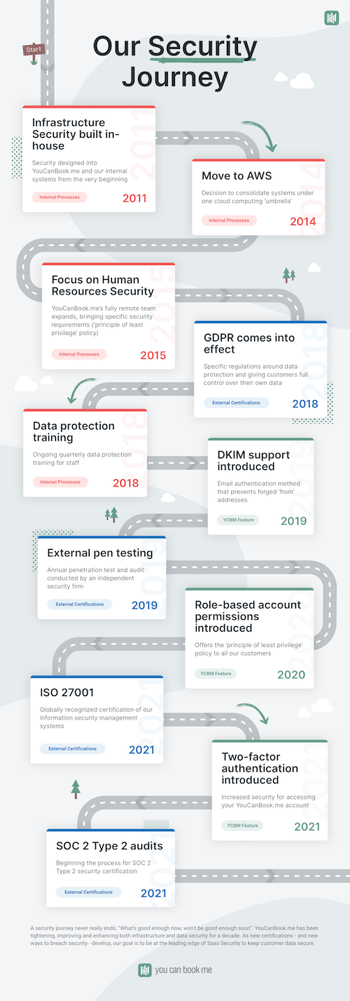
So the team set to work to identify the systems already in place, identify any gaps, and then start the process for external security certification, beginning with ISO 27001.
What a difference a decade makes
When YouCanBook.me began a decade ago, security issues were on a completely different order of magnitude than today. Even so, for CTO and co-founder Keith Harris, who built the tool himself, infrastructure security was always a central concern. In fact, Keith built his own password manager for the team to use before password managers were cool!
Over the years, the demand for industry-recognized certification, as well as the increasingly complex attempts by bad actors to access data, led YouCanBook.me to move engineer Antonio Acevedo into a full time role as Head of Infrastructure to keep a laser focus on security.
“It can be overwhelming,” says Antonio. “You have to be constantly looking at things that are happening, things that might be happening, things that no one has thought could happen.”
Internally: Start with NO
Security breaches aren’t just an external risk. It’s not enough to say we've closed down our systems; nobody can have unauthorized access. But yet, inside, everybody still has access.

A very clear strategy within the YouCanBook.me team is what they call the Principle of Least Privilege’ policy. This means there is a strict limit on user access for every area of the tool — basically, everything is forbidden by default.
“The philosophy is, unless there's a reason for somebody — including myself the CEO — to have access to data, particularly customer data, we just don't,” says Bridget. “Everything is compartmentalised so if you don't need to be in the room, you don’t get the keys.”
For Antonio, these security measures add complexity because he has to create access profiles for each role in the company. But it’s worth it.
“The Principle of Least Privilege is a huge mental lifesaver because you don't have to be thinking what might happen if this user does this or this one does that. No one is allowed to do anything unless they need to for their work.”
This might sound extreme but studies show that employees are one of your biggest security risks. Almost 90% of data breaches are caused by employee mistakes.
“It's an interesting balance for a customer-focused company,” says Keith. “Our Support team is highly motivated to help our customers. So they’re looking to have as much information as they possibly can to help with troubleshooting and solving problems. You have to tell them they're not allowed that data. It can feel like you’re tying their hands behind their back.

“So then you have to think about what changes you can make to the product that will help those customers without our team’s involvement. Troubleshooting has to suddenly go inside the product so the customer either no longer sees that problem, or they have the tools to solve it themselves and it doesn't require a human being to go in and do anything that could cause a data breach.”
Externally: Reducing the blast radius
If someone wants to attack you, they're going to attack you one way or another. So the point here is about making it so difficult that the attacker just moves on to the next company, goes somewhere else.
One of YouCanBook.me’s six values is Simple is Beautiful and that comes across strongly in their approach to infrastructure security.
One of Antonio’s first projects when he started at YouCanBook.me in 2014 was to migrate all their systems across to Amazon Web Services (AWS). The company has grown with AWS ever since, taking advantage of its ever increasing number of product solutions and its world-class reputation for SaaS Security.
“When you’re talking to customers and are able to say that you use AWS, it’s an easy discussion because everyone understands that means excellent security,” says Antonio. AWS operates a shared responsibility model which means they take care of security for specific components. “So we don’t have to worry about those components. We just have to focus on our own. And with highly configurable user access, we can keep to our Principle of Least Privilege.”
AWS offers a lot of solutions, but it doesn’t have everything. Sometimes, YouCanBook.me needs to choose another service.
“If we need to go outside the AWS umbrella, that’s fine. But it’s also where the extra security concerns come in. So you have to balance the benefits of using a different service with the potential risks it brings.”
Keep things simple. Keep them structured and siloed as much as possible and only come out of that when you really need to. It’s all about how you can reduce the blast radius of any attack.
One of the risks is passwords. Once again, human error rears its head. Passwords are one area that is really difficult to get right when you leave it to individuals.
“The tools outside AWS are why we use Dashlane,” says Antonio.
Dashlane is a password management tool that allows you to centralize permissions, easily giving or revoking employee access to passwords as required.
“We’re not a huge company but it doesn’t matter how many people you have. You still have to be able to track who has access to each tool, and when they accessed it. The more you close things down, the less you have to think about the likely scenarios where you’re going to be attacked. The ‘least privilege’ policy is about trying to narrow down the possibilities, so we can keep it manageable on our side.”
To ISO 27001... and beyond
YouCanBook.me’s policies - keeping a tight control over access management, ensuring the highest level of data security and being in a position to scale safely - are all included in the best practices outlined for Saas Security practitioners.
The logical next step for YouCanBook.me was to go for external certification of their security measures. The two options were ISO 27001 and SOC 2 certification.
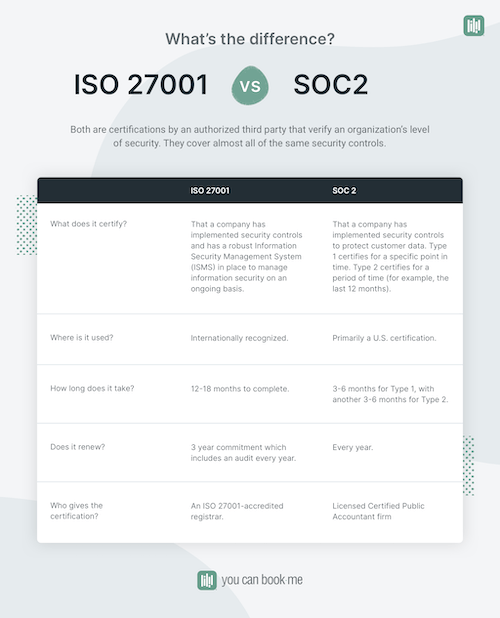
Any customer of a SaaS tool interested in security certifications will have seen those two names. What’s the difference between them? Actually, not a lot.
The SOC 2 and the ISO27001 certifications both convey industry-standard recognition that you have the security practices in place to protect customer data.
ISO 27001 certifies that a company has a robust Information Security Management System (ISMS) in place. It’s an internationally recognized three-year process with an initial pass/fail audit, and then an audit every year.
SOC 2 is a U.S. accreditation that focuses on proving that a company has implemented security controls to protect customer data. It is arguably harder to achieve, but you can have areas where you don’t yet conform. So it’s important to read the SOC2 certification for details on the areas where a company complies.
Achieving one of these certifications sets you well on the way to achieving the other, so Bridget decided to start with ISO 27001.
“One simple way to look at it is that SOC 2 is asking ‘Do you do what you say you do?’, whereas ISO 27001 is saying ‘Here’s what you should do’.
“ISO 27001 came with sort of an opinionated structure. And because we were going from a standing start with our Information Security Management System, that seemed to be a good place to begin.”
How did they wade through all the requirements to ensure they would pass the audit?
The company undergoes regular penetration testing of its systems, so for the past few years they had been tightening any security issues that those tests brought up.
For the audit, they hired a security consulting firm to help with the process. That team helped YouCanBook.me gather the existing information and knowledge within the company and translate that into Information Security-speak.
“A good example is recruiting,” says Bridget. “We have a lot of good, security-based procedures in our recruitment process, we just had never documented it in a way that described it as Human Resource Security.”
They also decided to purchase an Information Security Management System.
“We used ISMS.online, which we really recommend as a tool,” says Keith. “It is structured really specifically so it sets out all the areas that need to be covered and gives you a place for everything.”
Guided by ISMS.online’s framework, the team did a comprehensive review in every area that impacts information security:
- An employee practice audit to make sure all employees were aware of — and following — YCBM’s Information Security procedures
- An survey of third party suppliers to understand their security processes and certifications, and to make a call for each one whether they conformed with YCBM’s own policies
- An analysis of all policies and documentation that existed in various folders in other systems and then consolidated them into ISMS. online
- A comprehensive password management review to make sure all third party tools are correctly added to Dashlane, with Two-factor authentication switched on where available
- Deleting all unused third party supplier accounts
“We found that the rigour of having to take a root and branch look at what we were doing opened up new ways of thinking about what we do,” says Keith.
“For example, we moved our employee handbook into ISMS.online, and we took the opportunity to update our policies. Now there is a framework where everything interlinks. So it’s easy for auditors to review and easy for employees to access.”
YouCanBook.me is in a growth phase, increasing the number of team members and functions. So it felt natural to document the teams’ best practice as they went.
“It was a really good way for us to capture and write down some of the stuff that was going on inside people's heads. ISMS.online gave us lots of opportunities to do that”.
Was it difficult preparing a set of policies and procedures that would satisfy the ISO 27001 auditor?
Bridget admits that it can take a while to get into ‘ISO speak’. “But as soon as I got my head around what it was they were getting at, it was quite straightforward to produce the evidence we needed, and in many cases, that we already had in place.
“There was a whole series of little mini-joys: ‘Oh, we've got that already. All we need to do is write it down!’”
YouCanBook.me now uses ISMS.online as a central plank of the way the team works. It isn’t just a place for the auditor to check. It is actively used for policy development, project management and recruitment.
“It’s not always beautiful, but if you try to create this perfect online wiki, everything looks great. But when an auditor comes along and says, ‘Tell me how that relates to information security?’, you then struggle to extract out the glamour and noise. We decided to keep everything in this quite boring but very functional tool that follows closely the Information Security framework.”
What was the audit process like?
ISO certification is done by industry-approved bodies and it involves several multi-day audits.
“The auditor came in twice, for 2 and half days each time. They reviewed everything from online policies and systems, to physical controls in our workspace. They also interviewed a majority of the staff to make sure they were actively aware of and using the security procedures.”
When the review was finished, the auditor recommended that YouCanBook.me be certified as having met the requirements of ISO 27001.
SaaS Security is Forever
It was a great recognition of their work but, as Antonio cautions, SaaS Security never stops.
“What is good enough now, won’t be good enough soon. Bad actors are always coming up with new and more complex ways to attack. So you can never say ‘Okay we’re done. That's it.’”
The team has embarked on the next stage, to achieve SOC 2 - Type 2 certification, with the first audit due to be complete by the end of 2021. But the process has already made a lasting impact on the company in several areas.
Bridget says the whole company is now on alert. “We’ve all become a lot more aware of how some companies use — or misuse — our own personal data. We want to work for a company that treats other people's data with respect. So, we've now got a team that really supports what we do and actually I think there's been a lot of commitment internally, even beyond what's necessary for certification.”
With this focus, YouCanBook.me has fast-tracked features to improve account-level security for customers, including two-factor authentication (2FA) and role-based access for team members.
For Keith, the process resulted in much better business insights. “One surprise result for me was that we now have what is essentially quite a blue-chip, business level analysis on assets and risks.
“So even though it took quite a lot of work for us to do. We've done it now. And it's the kind of thing that I wouldn’t necessarily have expected a company of our size to have.”
And for Antonio, the focus on security has improved the way the team works. “It has changed our whole mindset. Now, we start thinking about security right at the beginning of the development process.
“All our updates and new features are now designed with security in mind. It’s called Shift Left Security. Not only do you get more secure code, but development is also much cheaper because you get a more complete solution the first time. You don’t have to go back later to introduce security into a working feature.”
Subscribe to our newsletter
Get productivity tips, news, articles and resources.
Written by
Kate Reynier
Kate is YouCanBookMe's Director of Product. She was YCBM's first employee and feels privileged to have been a part of the journey: from supporting our customers, to helping bring YCBM to life in our blog posts, and now helping to develop a product that our customer love.
Keep reading

7 Must-Have Coaching Software for Client Success
Streamline your business using these top coaching software, taking the admin tasks off your plate so you can focus on helping your clients become the best version of themselves.
Read bloge1f6.jpg)
Schedule Smarter: 7 Doodle Alternatives to Consider in 2024
On a quest to find the best scheduling tool for your team? Check out the seven best Doodle alternatives, all designed to help you save time and hassle!
Read blog
4 Reasons Why YouCanBookMe Is Better Than Calendly
If you're a small business that truly care about your customers, Calendly isn't the right scheduling tool for you. See why YouCanBookMe is better than Calendly on four major fronts.
Read blog